iRecorder debuted on the Play Store, promising a safe and user-friendly application. In its early days, the app appeared completely harmless, winning the trust of many users worldwide. However, as the months passed, the true colors of this seemingly benign application started to show.
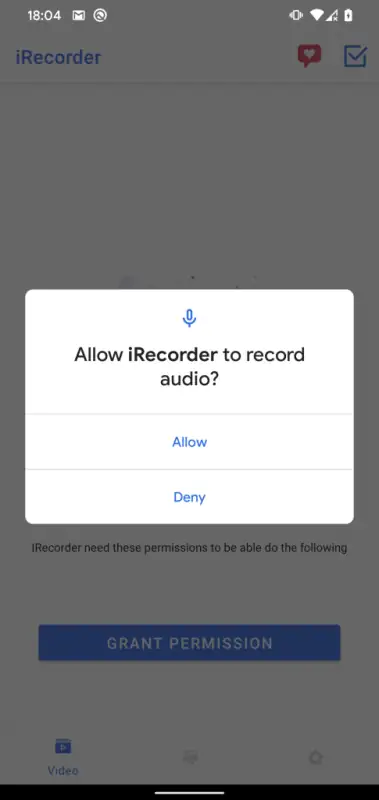
Unbeknownst to many users, the iRecorder app underwent a sinister transformation. It metamorphosed into a potent piece of spyware, breaching the boundaries of privacy and security for its users. The app would quietly spring into action every 15 minutes, covertly capturing audio recordings of the unsuspecting users.
Once these audio snippets were recorded, the app stored these private audio recordings on the server maintained by the app’s developer. What was once considered a safe and harmless app had now become a silent infiltrator, secretly prying into the personal lives of its users every quarter of an hour.
ESET researcher Lukas Stefanko was the first to reveal this nefarious conduct. He chronicled this malicious behavior in a detailed blog post, showing it to the world. According to his write-up, the app had already weaved its way into the devices of over 50,000 unsuspecting individuals.
iRecorder – Screen Recorder, by its full Play Store name, was initially launched as a straightforward screen recording tool. The concept was simple: offer users a way to record what’s happening on their device screens. When the app launched in 2021, it worked like any other similar app. Users downloaded it, trusting it to perform the simple task of screen recording, without any clue of its veiled intentions.
But things took a sinister turn in August 2022 when an update was released for the app, the version being 1.3.8. This was no ordinary update; it brought many harmful features, turning the app into a genuine security threat for users.
What made this update particularly harmful was the inclusion of some tailor-made malicious code. This damaging code was ingeniously added into the app’s software, making it nearly impossible for the average user to detect. What is the source of this harmful code? It was based on a freely available open-source Android remote access trojan (RAT), aptly named AhMyth.
AhMyth, a notorious RAT, was notorious in cybersecurity circles for its ability to control devices without the user’s knowledge. In the case of iRecorder – Screen Recorder, this harmful software took on a new identity, becoming known as AhRat.
Upon discovering the troubling transformation of iRecorder, ESET promptly alerted Google about the malicious activities within the app. Acting swiftly, Google removed the app from the Play Store, ensuring no more unsuspecting users would fall prey to its deceptive behavior.
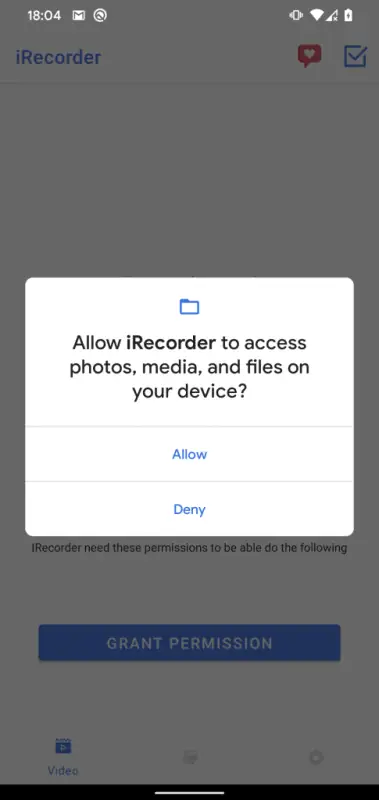
However, despite its removal from the store, the app poses a considerable threat. The dangers remain quite real for those who already have it installed on their devices. The app can breach user privacy, giving it a free pass to access personal files and record audio clandestinely.
According to the detailed report by ESET, the app’s deceptive behavior extends further. It actively seeks and extracts audio recordings from the device’s microphone and fishes for files bearing specific extensions. These extensions correspond to saved web pages, images, audio and video files, and various documents – a treasure trove of personal data.
Once this data has been stolen, the app transfers it back to a remote server. This server, controlled by the app’s developers, receives and stores this wealth of stolen information. We’re not sure if the developers are selling the data stolen or more than that, but if you have this app installed, remove it immediately from your device.
We’ve also searched for the app on Google and found it on multiple sites that host APKs for various applications that aren’t on the Play Store anymore. If you need a good screen recorder for Android, we recommend AZ Recorder or XRecorder.